Last updated by: buvan008, Last updated on: 08/09/2024
Redback Operations General Incident Response Playbook
Redback Operations General Incident Response Playbook For Purple Team
Effective Date: 29 April 2024. Last Edited: 10 May 2024. Author: Priyanshu Document Reference: ROGIR-1. Expiry Date: 12 May 2025. Version: 1.0.
Introduction
1.1 Overview
In today's connected digital environment, the risk of cyber security breaches is high for organizations of all sizes and industries. Redback Operations, like many others, operates in an environment where potential security breaches and disruptions are a constant concern. Whether it's a sophisticated cyber-attack triggered by external threats, or an unintentional data leak caused by the carelessness of insiders, the consequences of a security breach can be severe, from financial loss to reputational damage.Because these challenges must be faced, the Redback Operation Recovery Playbook has been carefully crafted as a comprehensive guide to navigating the complex landscape of incident response and recovery. The manual is primarily designed to equip Redback Operations with the tools, strategies, and best practices needed to effectively restore systems,data, and operations after a security breach. By creating a structured framework for response and recovery efforts, the manual aims to empower Redback Operations to mitigate the impact of incidents, minimize downtime and protect against future threats.
1.2 Purpose
The Redback Operation Recovery Playbook has one purpose at its heart: to create a unified and coordinated approach to recovery operations. As events unfold and disrupt normal operations, the playbook acts as a guiding beacon, providing clear instructions and actionable steps to help you navigate the turbulent waters of disruption. Its overall goal is to ensure that Redback Operations are well prepared to weather the storm of security breaches and, on the other hand, stronger and more resilient.
The combination of proactive measures and reactive strategies aims to equip Redback Operations with the necessary flexibility to withstand and recover from various security incidents. Whether it's a targeted cyber-attack to steal sensitive data or a system failure that threatens to shut down operations, the guide provides a response and recovery plan that is both robust and adaptive.
1.3 Definition of Attack
In the context of the Redback Operation Recovery Manual, the term "attack" includes a broad spectrum of malicious actions that threaten the security, integrity or availability of Redback's systems and networks. . or data. The guidance recognizes the multifaceted nature of security breaches, from intentional actions by external threat actors attempting to exploit vulnerabilities to inadvertent errors by internal users who inadvertently expose sensitive information. By adopting a broad definition of attacks, the playbook ensures that response efforts are not limited to traditional cyber threat concepts, but instead target the various risks that Redback Operations face. This comprehensive approach enables a more holistic understanding of security incidents and empowers response teams to effectively address all threats, whether they originate from within or outside the organization.
1.4 Scope
The scope of the Redback Operation Recovery Playbook is intentionally broad to cover all types of security incidents and disruptions that affect Redback operations. This includes, but is not limited to, events resulting from malicious activity such as cyber-attacks, data breaches and phishing attempts, as well as non-malicious events such as system failures, natural disasters, and human error. By casting a wide net, the playbook ensures that narrow definitions or biases do not limit security response efforts. Instead, it considers the complexity and unpredictability of today's threat landscape and recognizes that security breaches can manifest in many forms and require a flexible and adaptive response.
Basically, the introduction provides a comprehensive overview of the Redback Operation Recovery Playbook, outlining its purpose, scope, and approach to handling security incidents. It sets the scene for the rest of the document and sets the stage for the detailed strategies and procedures that follow.
2 Attack Types
2.1 Insider Threat
Insider threats are of particular concern to Redback because people within an organization can misuse their access rights to compromise security, integrity, or availability of Redback's systems, networks, or data. These individuals may include employees, contractors, or other trusted entities that pose a serious threat to the organization's cybersecurity posture. Insider threats come in many forms, including unauthorized access to confidential information, data breaches, obstruction, and negligence. For example, employees can directly access Redback systems and abuse their rights to steal confidential data for personal gain or inadvertently reveal confidential information by tampering with company assets. Detecting and mitigating insider threats requires a multi-layered approach that includes implementing strong access controls, monitoring user activity, and conducting regular security briefings, and creating a culture of accountability and trust within the organization.
2.2 External Attacks
External attacks against Redback originate from threat actors outside the organization's domain, including followers, Internet critics, and domestic actors. These attackers often exploit vulnerabilities in Redback's systems, networks, or applications to gain unauthorized access, steal sensitive information, or disrupt operations. External attacks come in many forms, including phishing attacks, malware, denial-of-service (DoS) attacks, and exploiting software vulnerabilities. For example, attackers could launch sophisticated cyberattacks on Redback's network infrastructure, using untouched software vulnerabilities to access sensitive data or disrupt critical business operations. Protecting against external attacks requires a proactive, multifaceted approach, including implementing cybersecurity controls, conducting regular vulnerability assessments, monitoring suspicious activity, and using threat intelligence to identify and mitigate emerging threats.
2.3 Data Breach
Data breaches are a serious threat to Redback's security posture due to the unauthorized access, deletion, or disclosure of sensitive or confidential information. These breaches can occur from multiple attack vectors, including external attacks, insider threats, and accidental data exposure. A data breach can have serious consequences for Redback, including financial loss, reputational damage, legal penalties, and loss of customer trust. For example, cybercriminals could exploit vulnerabilities in Redback's network infrastructure to gain unauthorized access to customer databases and steal sensitive information such as personally identifiable information (PII), payment card data, inventory, or mind. Preventing and mitigating data breaches requires a multilayered approach, including implementing strong access controls, encrypting sensitive data, monitoring for unauthorized access, conducting regular security audits, and adhering to regulatory compliance requirements such as GDPR or CCPA.
2.4 Phishing Attacks
Phishing attacks are a prevalent form of cyber threat that targets individuals within Redback through deceptive tactics, such as fraudulent emails, messages, or websites, with the goal of tricking recipients into divulging sensitive information or performing malicious actions. These attacks often impersonate legitimate entities, such as Redback's employees, customers, or business partners, to gain the trust of unsuspecting victims. Phishing attacks can take various forms, including email phishing, spear phishing, or social media phishing, and may involve enticing recipients to click on malicious links, download malwareinfected attachments, or enter login credentials into fraudulent websites. For example, a cybercriminal may send a phishing email to Redback's employees, posing as the IT department and requesting them to reset their passwords by clicking on a malicious link, thereby compromising their credentials, and gaining unauthorized access to Redback's systems. Preventing phishing attacks requires a combination of user education and awareness training with technical capabilities, such as email filtering, web content analysis, and endpoint protection, to help people recognize and report phishing attempts.
2.5 Ransomware Attack
Ransomware attacks are a serious threat to Redback's operations by distributing malicious software that encrypts files or systems and makes them inaccessible until payment is made. striker These attacks can cause damage to Redback, including data loss, financial damage, organizational disruption, and reputational damage. Ransomware attacks can be delivered through various methods, including email phishing, packet exploits, and remote desktop protocol (RDP) vulnerabilities, which can target endpoints, servers, and Redback network infrastructure. For example, cybercriminals can distribute ransomware to Redback employees using phishing emails with malicious attachments. Once opened, the attachment encrypts files on the victim's device and demands a ransom in exchange for the decryption key. Preventing ransomware attacks requires a multi-layered approach, including implementing end-to-end security measures, backing up sensitive data, patching known vulnerabilities, and segmenting networks to prevent the spread of ransomware and staff training on ransomware risks and best practices. epidemic
2.6 Credential Theft
Unauthorized removal or misuse of login credentials, such as usernames and passwords, to access a secure Redback State site. Systems, applications, or sensitive information. These credentials can be obtained in several ways, including phishing attacks, hacking techniques, or exploiting vulnerabilities in the authentication method. Identitytheft allows attackers to impersonate legitimate users, bypass security controls, and gain unauthorized access to Redback resources. For example, cybercriminals can use stolen credentials to log into the Redback employee portal and download sensitive. data or initiate fraudulent activities. To prevent information theft, you should implement strong authentication methods, including multifactor authentication MFA,password management policies, and user training to educate employees on the importance of protecting their symptoms and being aware of potential threats.
Basically, Redback Operations implements cybersecurity measures and enforces security to stay alert against all types of attacks, including insider threats, external attacks, data breaches, phishing attacks, ransomware attacks, and theft to stay on top of day. Aculture of security awareness throughout the organization.
3 Stakeholders
The proficient handling and settlement of incidents require the coordinated endeavours and cooperation of a heterogeneous group of stakeholders, each possessing distinct knowledge, viewpoints, and roles. The following parties are essential to the incident response process, from frontline responders entrusted with containment and mitigation to senior leadership tasked with making strategic decisions:
- IT Security Team: Redback Operations' IT Security Team is a key element of incident response, spearheading the technical efforts to locate, investigate, and resolve problems involving improper usage. This team oversees monitoring system and network logs, doing forensic investigation, and implementing security procedures to prevent such incidents in the future. They work together with other relevant parties to guarantee a coordinated and effective response to instances of inappropriate usage, minimising the impact on Redback's operations and data protection.
- Incident Response Team: The cross-functional incident response team at Redback Operations is made up of representatives from the management, IT, security, and legal departments. This group is responsible for planning incident response actions, communicating with pertinent stakeholders, and making critical decisions to contain and handle instances of inappropriate use. They ensure that incident response operations adhere to Redback's policies, procedures, and legal obligations, fostering a cohesive and efficient response.
- Legal and Compliance Department The management, IT, security, and legal departments are represented on Redback Operations' cross-functional incident response team. To contain and manage cases of inappropriate use, this group oversees organising incident response actions, corresponding with relevant parties, and making crucial decisions. To promote a coordinated and effective reaction, they make sure that incident response activities follow Redback's rules, processes, and legal duties.
- System Administrators: Root access concerns are largely identified, investigated, and resolved by system administrators, who operate as stewards of organisational systems and networks, using their technical expertise and domain experience to restore system integrity and performance.
- Management: Setting organisational priorities, allocating resources, and spearheading strategic efforts aimed at bolstering the organization's resilience against root access threats are all crucial tasks performed by executive leadership, which includes C-suite executives and senior management.
- External Consultants: Organisations may hire outside consultants or third-party vendors to supplement their incident response capabilities in situations requiring specific knowledge or resources. These vendors can help with forensic analysis, threat intelligence, and remediation efforts.
4. Flow Chart
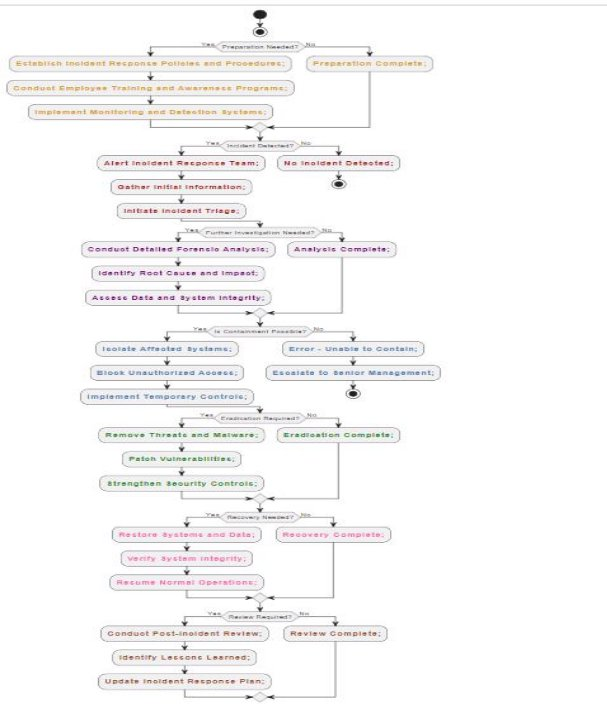
- Preparation Stage (Yellow):
- This phase involves the first steps in becoming ready to handle any issue that may arise with Redback's systems.
- Establishing the incident response team, creating crisis response protocols, running training sessions and simulations, and putting security and surveillance technologies in place are important tasks.
- The necessity of readiness and preparation for the efficient handling of situations is symbolised by the colour yellow.
- Detection Stage (Red):
- Identifying signs of inappropriate use or illegal access to Redback's systems and resources is the main goal at this point.
- Using intrusion detection systems (IDS) and security information and event management (SIEM) technologies, keeping an eye out for suspicious activity, and examining anomalies and warnings are some of the actions involved.
- Red is a symbol for the urgency and importance of event detection to provide quick mitigation and response actions.
- Analysis Stage (Violet):
- This stage entails determining the type and extent of the incident that has been discovered.
- Data collection, forensic analysis, system and network analysis, threat actor strategies, and indicator of compromise (IOC) identification are among the activities involved.
- The colour violet represents the necessity for a careful investigation to ascertain the incident's causes, consequences, and authorship.
- Containment Stage (Sky Blue):
- At this point, measures are being done to lessen the incident's impact and stop more unauthorised access or data leaks.
- To contain or prevent harmful software or data, segregate susceptible systems, put access restrictions in place, and, if containment fails, escalate to senior management.
- The containment strategies intended to lessen the incident's impact and spread are symbolised by the colour sky blue.
- Eradication Stage (Light Green):
- This phase concentrates on eliminating attackers from Redback's networks and infrastructure and resolving any risks or vulnerabilities that may still exist after the event has been controlled.
- Among the tasks include deleting illegal software and data, patching, or upgrading weak systems, and examining and revising security guidelines and protocols.
- The activity of eliminating the event and guaranteeing the security of the organization's systems is represented by the colour light green.
- Recovery Stage (Pink):
- Restoring impacted systems and data to normal functioning and continuing company operations are the goals of the recovery stage.
- Rebuilding or reconfiguring networks and systems, recovering corrupted systems and data backups, and putting user awareness and education programmes into action are among the tasks.
- The process of recuperating from the catastrophe and improving security procedures to lessen the possibility of a recurrence is symbolised by the colour pink.
- Post-Incident Review Stage (Brown):
- Post-incident activities are carried out in the last step to assess the organization's reaction to the incident and pinpoint areas that require improvement.
- The process of responding to incidents is thoroughly analysed, best practices and lessons gained are documented, and incident response protocols, rules, and security configurations are updated, among other tasks.
- The post-event initiatives intended to improve future response efforts and learn from the occurrence are represented by the colour brown.
5. Incident Response Stages
1. Preparation
- Objective: Putting in place the guidelines, practices, and tools required to handle issues in Redback's systems.
- Activities:
- Putting together a team for incident response with clear roles and duties.
- Creating strategies and processes for crisis response, such as escalation routes and communication guidelines.
- Holding practice sessions and exercises on a regular basis to guarantee readiness and rehearse incident response protocols.
- Putting in place security measures and surveillance systems to find and stop events.
- Outcome: A well-equipped company with the ability to react to situations quickly and efficiently.
2. Detection
- Objective: Recognising warning signs of illegal access to Redback's resources and systems.
- Activities:
- Keeping an eye out for questionable activity, such as odd access patterns or unauthorised attempts at authentication.**
- Using security information and event management (SIEM) and intrusion detection systems (IDS) to find such problems.**
- Examining abnormalities and warnings to distinguish between authorised and unauthorised activity.**
- Outcome: Rapid reaction times and mitigating actions are made possible by early event detection.
3. Analysis
-
Objective: Recognising the type and extent of the incident that occurred.
-
Activities:
-
Gathering information and carrying out forensic investigation to ascertain the origin and degree of the illegal entry.**
-
Examining hacked networks and systems to find attack vectors and how they affect compromised data.
-
Recognising the tactics, methods, and procedures (TTPs) of threat actors and indicators of compromise (IOCs).
-
Outcome: A thorough comprehension of the event, considering its causes, consequences, and attributions.
4. Containment
- Objective: Limiting the spread and effects of the incident and stopping any illegal access or data leaks.**
- Activities:
- Dividing up susceptible networks and systems to stop intruders from moving laterally.**
- Putting safety measures and access restrictions in place to stop illegal access to sensitive data.**
- Limiting or preventing harmful data, software, or network flow to stop more damage.**
- Outcome: Efficient handling of the situation to reduce harm to Redback's systems and data.
5. Eradication
- Objective: Eliminating threats and any lingering vulnerabilities from Redback's networks and IT systems.**
- Activities:
- Removing illegal access and putting compromised systems back in a safe and secure condition.**
- Upgrading or patching susceptible systems and software to stop further exploitation.
- Examining and revising security protocols and guidelines to fix flaws or vulnerabilities found.
- Outcome: Eradicating all evidence of the incident and minimising weaknesses to stop it from happening again.
6. Recovery
-
Objective: Restarting company operations and returning impacted systems and data to normal functioning.
-
Activities:
-
Restoring damaged systems and data backups to guarantee the integrity and accessibility of data.
-
Rebuilding or rearranging networks and systems to improve security and stop such incidents in the future.
-
Putting user awareness and education programmes into action to reduce unauthorised access events in the future.
-
Outcome: Full restoration of operations and services, together with strengthened security measures to lessen the chance of recurrence.
7. Post-Incident Review
- Objective: Assessing the organization's reaction to the event, noting lessons gained and opportunities for development.**
- Activities:
- Evaluating the incident response procedure in-depth to find its advantages, disadvantages, and potential areas for development.
- Recording best practices and lessons discovered to improve incident response skills in the future.
- Modifying security setups, rules, and incident response protocols considering review results.
- Outcome: Improved capacity for responding to crises and preparedness for new ones.
6. Terminology
Terminology in incident response encompasses a range of concepts and terms essential for effective communication and understanding within the cybersecurity domain. It provides a common language for incident responders, enabling precise and unambiguous communication during incident response activities.
- An essential part of Redback Operations' cybersecurity setup is an intrusion detection system (IDS). IDS keeps an eye on network traffic to look for indications of malicious activity, unauthorised access, or security lapses. Network packets and system logs are analysed by IDS to find anomalies or patterns that point to possible security risks. When an improper usage occurrence occurs, Redback's occurrence Response Team can investigate and take appropriate action based on the alarms generated by IDS.
- SIEM, or Security Information and Event Management, is essential to Redback's incident response operations. SIEM provides real-time visibility into security incidents by gathering, correlating, and analysing security event data from several sources throughout the IT architecture of the company. SIEM improves Redback's overall security posture and resilience against improper usage incidents by aggregating and correlating security data, making it easier to identify and respond to security threats.
- Redback uses vulnerability assessment as a preventative strategy to find and fix security flaws in its networks and systems. Redback performs vulnerability assessments to find known vulnerabilities, misconfigurations, or weaknesses that threat actors could exploit through routine scanning and analysis. Redback improves its security defences and lowers the possibility of improper usage situations by prioritising remediation activities according to the severity and impact of vulnerabilities.
- Redback's cybersecurity defences face a substantial challenge from zero-day vulnerabilities. These vulnerabilities are security holes in software or systems that were previously undiscovered or revealed, making organisations open to abuse by hostile parties. Redback keeps a quick response capability to handle new threats and continually searches for zero-day vulnerabilities. Redback increases its resilience against sophisticated cyber threats and reduces the danger caused by zero-day vulnerabilities by putting proactive measures like threat intelligence sharing and patch management into place.